Thursday, 24 April 2014
The EXPTA {blog}: How to Boot Directly into Desktop with Windows Ser...
The EXPTA {blog}: How to Boot Directly into Desktop with Windows Ser...: I love Windows Server 2012 RTM, I really do. But who's bright idea was it to boot to the "Modern UI" (aka, Metro) instead ...
Monday, 21 April 2014
Monday, 7 April 2014
Roaming Profiles versus Local Profiles
In a Windows network environment, there are many pros and cons involving the use of roaming profiles versus local profiles. In addition to the security matters, there are issues with data loss, file storage, bandwidth, and more. In this article, I will discuss some of the things I have run across in my work in the IT field.
A user profile is a collection of data specific to one user. This includes data like your Favorites in Internet Explorer, your Outlook settings, and so on. Windows is designed to store each user’s data in one location, such as the computer’s hard drive or on a server. When you log into a computer, it loads your user profile data along with whatever software you have set to load at startup.
In case you didn’t know, a roaming profile is a user profile that is stored on a server, and it is downloaded to the PC whenever a user logs in. This way, the user can access their information and settings no matter what computer they log into. A local profile is one that is stored just on one computer, and very little data is transmitted between the PC and the server when the users logs on.
Roaming Profiles
Pros:
Automatically backs up user data to the server whenever they log out, so that the user doesn’t have to remember to do so.
Allows users to log into multiple computers. This works great in an environment where people don’t have designated desks, such as an open lab.
Cons:
Security issues. After the user has logged on, a copy of their profile is left on the hard drive. If the computer were to be stolen, this data could easily be compromised.
Slow login times. If a user puts too much data in their profile, it could take a very long time to transfer all that data whenever they log on or off. This could lead to profile corruption.
Bandwidth consumption. Large user profiles take a lot of network bandwidth to transfer data back and forth. Much of this is amounts to wasted bandwidth since many of the files and data transferred are not accessed every time the user logs on.
Maintenance issues. I regularly have to clean old profiles off some computers because those profiles left behind fill the hard drive so much that they prevent other people from logging in. It’s also a fairly regularly problem to have to rebuild user profiles after data has been corrupted during transfer.
Local Profiles
Pros:
Allows for much faster login times because the user’s data is all stored locally.
Cuts down on bandwidth consumption because less data is transferred during login and logoff.
Great for people who have a designated desk where they use the same computer every time.
Cons:
If the user gets on a different PC, they may not be able to access their local data unless they stored some of it on a separate folder on a server.
Security issues. Having all the data stored locally presents a security problem if that PC is stolen.
Potential for data loss. I distinctly remember several people losing important customer data after their computers were destroyed by Hurricane Katrina. These users had been storing data on their hard drives and had no backup copies. When their PC was literally submerged by flood waters, their data washed away with the rest of the machine.
Conclusion
There are as many reasons to use roaming profiles as there are to use local profiles. There are equally as many reasons not to use one over the other. Personally, I think the best solution for a network environment is to provide network server locations for all data storage, then it won’t so much matter if the users are on roaming or local profiles.
The important thing is that users should only be allowed to store a very minimal amount of data in their profile, because it is safer and more secure to keep their data on the server. That way, it doesn’t matter what computer they log into because they can still access their data, and they won’t have to wait for it to download to their machine.
Furthermore, it may help to ‘lock down’ the PC so that the user will be severely limited as to where they store their data. One major problem with roaming profiles is that users tend to dump a lot of data on their Desktop, and this data gets transferred every time they log into a different machine. Users simply should not put any files on the hard drive, and it may require some training in regard to file locations to make sure they don’t do this. Often times, issues with data loss or security breaches come about simply because the user didn’t know what they were doing.
Microsoft Outlook Password Decryptor (Free)
| ||
| Outlook stores the password for subsequent logins when user selects the 'Remember Password' option during authentication. The password is stored in the encrypted format and only respective user can decrypt the password. Outlook Password Decryptor can instantly decrypt and recover all these account passwords. For command-line version, check out our new tool - Outlook Password Dump. It can recover passwords from all versions starting with 'Outlook Express' to latest version,Outlook 2013. It works on both 32-bit and 64-bit platforms starting from Windows XP to Windows 8. | ||
| Features | ||
| Outlook Password Decryptor is the all-in-one tool to recover passwords from all versions of Outlook. Also it can decrypt passwords from different type of Email account configurations supported by Outlook, such as | ||
| ||
| On starting, it automatically detects the current Outlook version along with user & platform information. It also provides option to save the recovered password list to HTML/TEXT /XML/CSV file for future use. | ||
| Outlook Account Password Location | ||
Different versions of Outlook uses different location and mechanism to store the account password along with other details such as email and server information.
Outlook Express, 98 and 2000 versions store the remembered password in the 'Windows Protected Storage' similar to older versions of Internet Explorer. The password link and other account information are stored at one of the below mentioned registry locations. | ||
| HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts HKEY_CURRENT_USER\Software\Microsoft\Office\Outlook\OMI Account Manager\Accounts | ||
| Outlook version starting from 2002 to 2010 stores the account password (other than Exchange Server) in encrypted format at following profile location | ||
| [Windows NT onwards] HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles [Prior to Windows NT] HKEY_CURRENT_USER\Software\Microsoft\Windows Messaging Subsystem\Profiles | ||
| Latest Outlook 2013 (version 15.0) stores the account configuration along with encrypted password at following location | ||
| HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Outlook\Profiles\Outlook | ||
| Newer versions of Outlook store the 'Exchange Server' based passwords in the credential provider (like network passwords) which is more secure than other methods. For more internal details on how OutlookPasswordDecryptor decrypts these passwords read the following research article, 'Exposing the Secret of Decrypting Outlook Passwords' | ||
| Installation & Uninstallation | ||
| It comes with Installer so that you can install it locally on your system for regular usage. This installer has intuitive wizard which guides you through series of steps in completion of installation. | ||
| At any point of time, you can uninstall the product using the Uninstaller located at following location (by default) | ||
| [Windows 32 bit] C:\Program Files\SecurityXploded\OutlookPasswordDecryptor [Windows 64 bit] C:\Program Files (x86)\SecurityXploded\OutlookPasswordDecryptor | ||
| How to Use? | ||
It is very simple and easy to use.. You can just start it by double clicking on the executable file.
Here are the brief usage details.... | ||
| ||
| For command-line version, check out our new tool - Outlook Password Dump. | ||
| Screenshots | ||
| Screenshot 1: Outlook Password Decryptor showing the recovered passwords from different type email accounts stored by Outlook. | ||
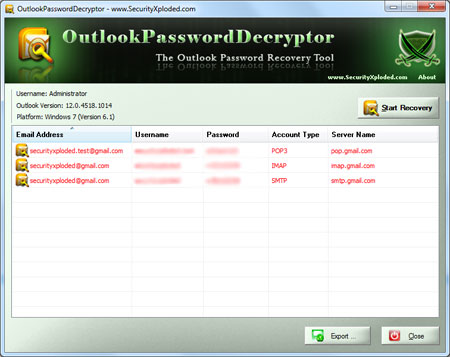 |
Wifi Security, Home Network Issues
Wi-Fi security, how the IT bods keep their home network secure.
If you’re the most tech savvy person in your family the chances are you are regularly cast into the role of unofficial family technical support.
It doesn’t matter how much or how little you know – as long as you are more technically competent than the rest of your family you’ve got a job for life.

You’ll help their laptops find printers, dig out files that have disappeared inexplicably, tell them why the internet doesn’t work (“…it was working yesterday!”), and clean up viruses.
And that, in our modern and interconnected world, makes you part of the cyber security front line.
Much of the work we conduct at CP revolves around network security and ensuring organisations are protecting themselves, their users and the data transmitted. We all have homes to go to, so it’s good to review the simple but important things that all of us who act as our family’s unofficial technical support and cyber-defence team can do to make things harder for the bad guys.
1. Check computers for zombies and other malware
Most people seem to be using anti-virus software these days but the software is only as good as its most recent update.
If your family members have subscriptions that have expired, if they haven’t done a baseline check lately, or if they’re Mac, tablet or smartphone users and think they aren’t vulnerable, get them a reputable product, bring it up to date and do a check for zombies and other malware today.
(We recommend AVAST as it’s kept our network clean and tidy since we began using it)
2. Enable WPA or WPA2 on home WiFi
If anyone in your family is using unsecured home WiFi or has secured their WiFi with WEP encryption, take two minutes to switch them to WPA or WPA2 today.
If you think you have already set up WPA for them, go and check they haven’t done a factory reset or anything that might have undone your work.
3. Set different passwords for every website
Make sure your family members are using different, strong, passwords for each website they log into. Thieves will often try stolen passwords on a range of popular websites because they know that people reuse them.
Help your family choose strong passwords that are at least twelve characters long and made up of a mixture of letters, numbers and special characters. If they have trouble remembering passwords then consider a password manager like LastPass or KeePass.
Of course, security doesn’t end with our three essentials, so let’s finish with a fourth…
Subscribe to:
Posts (Atom)